High Secure Authentication Algorithm - In Memory Authentication
Authentication systems are essential for security. If there's a problem with them, it can cause significant issues. In this topic, we'll discuss a secure authentication system design that can't be manipulated by outsiders.
Instead of sharing code, I'll explain the system design and its functionality. Prior experience with Http Protocol, cookies, server/client communication, and Jwt (Json Web Tokens) will be helpful for understanding this topic.
If we explain algorithm of this technique in 2 phases:
Phase 1
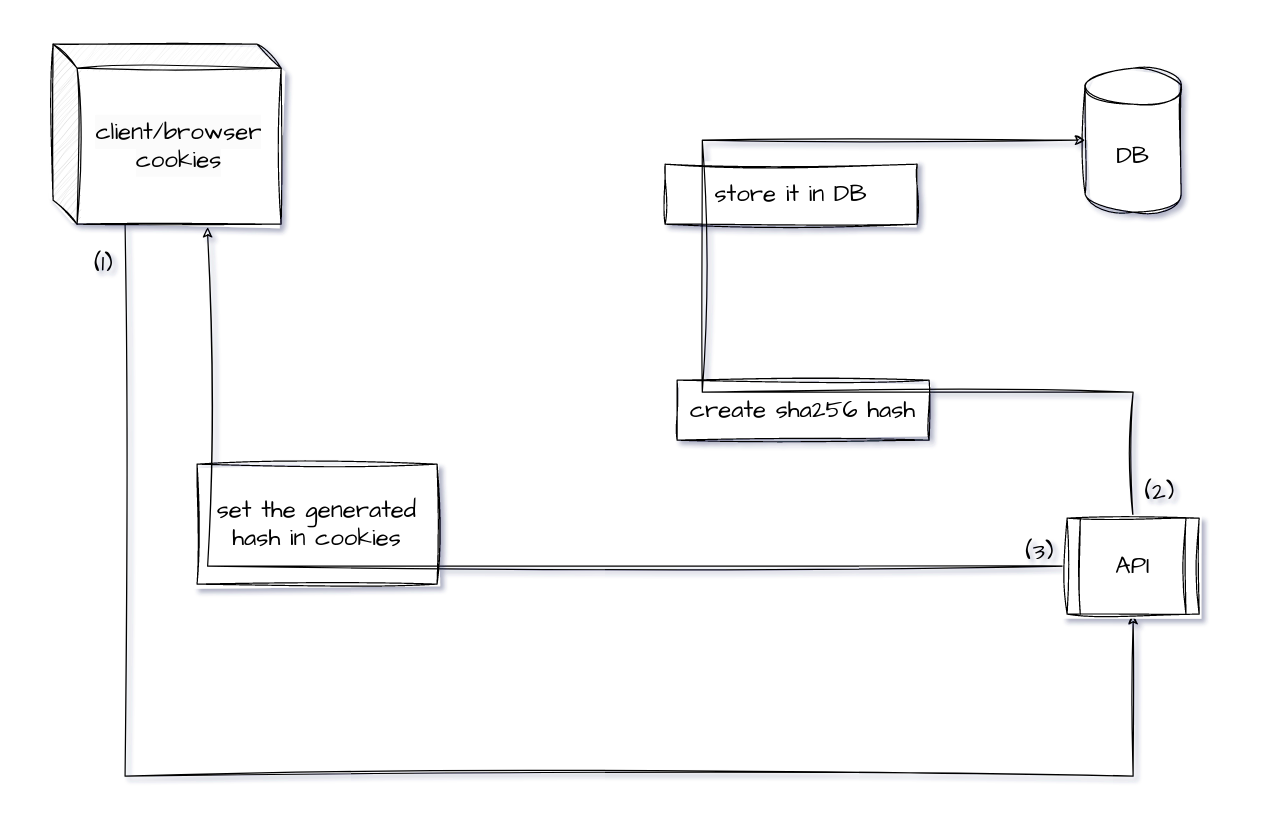
Explanation of the processes that occur in the diagram above:
- Client sends a request to the server.
- Server creates a unique(e.g, sha256) value for the requesting user and writes it as refresh token in the database where user information is kept.
- Server sets the token which created in the previous step as refresh token to client/browser cookies with http only and secure flags during the response process.
Phase 2
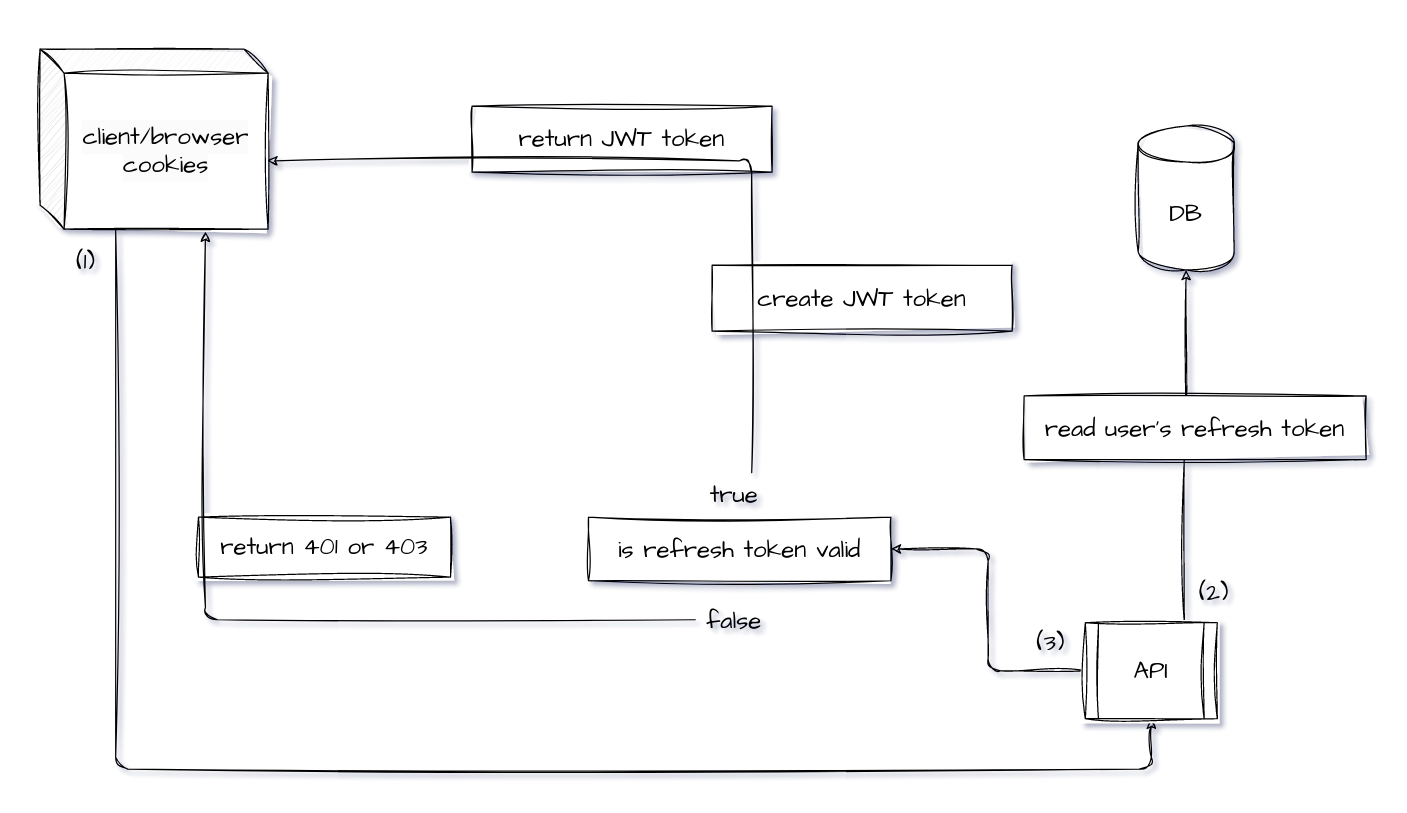
Explanation of the processes that occur in the diagram above:
- Client side sends a request to the server.
- Server side reads the refresh token from cookies and compares it with the one in the database table where the user data is kept.
- If tokens does not match, returns 401 or 403.
- If it does match, then server creates an access token using JWT(with very short expiration time) and returns it to the client.
- Client side,
- If the response is 200, assigns the access token in a variable(avoid sharing this value with any service or browser storage) and uses it from memory whenever it's needed.
What we will achieve from process cycle specified in the phases above:
- 3rd party can not access to access token because it kept in computer/device's memory.
- 3rd party can not access to refresh token because it's settled with http only and secure flag in the cookies.
- 3rd party can not create access token because this process requires refresh token which can only be generated from initial authorization(like signing in) from server.